Table of Contents
Common Database Server Threats
What Are the Requirements for Data
Security?
What Are the Steps Toward Data
Security?
Check List of Actions for IT
Security and Database Security
Business Continuity and Disaster
Recovery Planning
Policies, Procedures, and Training
Memorandum
Date: May 12, 2004
To: Mr. Kerwin Ewo, Chief Technology Officer, Gentronics, Inc.
From: William F. Slater, III, IT Consultant
Subject: Addressing Security Issues to Protect Database Assets
Dear Kerwin,
As we have discussed in conversation and in e-mail, I feel strongly that Gentronics needs to do a better job of treating data as a corporate asset. In my previous memo, I discussed the importance of utilizing a data dictionary and data normalization techniques as a means of ensuring our data was treated more like a corporate asset. In this memo, I want to address something of even greater importance: providing the best possible security for our corporate databases.
This attachment to this memo will describe some important concepts about data and database security, as well as the other levels of IT security that must be reviewed in order for these practices to be effective.
It may help to remind you that as an IT professional, who has been in this IT business since July 1977, I am particularly interested in and involved in IT security. As a result I continue to pursue knowledge, experience, and excellence in this area. For example, I am a System Security Certified Practitioner, and I will take the CISSP exam on June 20, 2004.
I look forward to our discussions following your review of this memo and the attachment.
Regards,
William F. Slater, III, SSCP
IT Consultant
ATTACHMENT
Introduction
The area of IT security is one of the fastest growing areas of information technology and with good reason: as our systems have become more complex, greater in number, and more distributed, the ability to exploit them has grown exponentially. In fact, because of the Internet and World Wide Web phenomenon, miscreants as young as early teens, can use virus and/or worm kits to easily create software that can inflict damages in the tens of millions of dollars, just for the fun of it. People are also engage in industrial espionage, attempting to steal secrets via weaknesses in corporate networks. And it is also a fact that terrorists, as well as countries with issues against the U.S., train hackers daily in tactics of cyber warfare. So there has never been a time where IT security was more important, or more challenging, than the times in which we are now living.
This memo attachment will cover some important IT security concepts and what steps should be covered to make Gentronics databases more secure in such a dangerous world.
Definition of Security
In the present, IT security has three dimensions: Confidentiality, Integrity, and Availability. This is best remembered by the acronym, “CIA” (Escamilla, 1998).
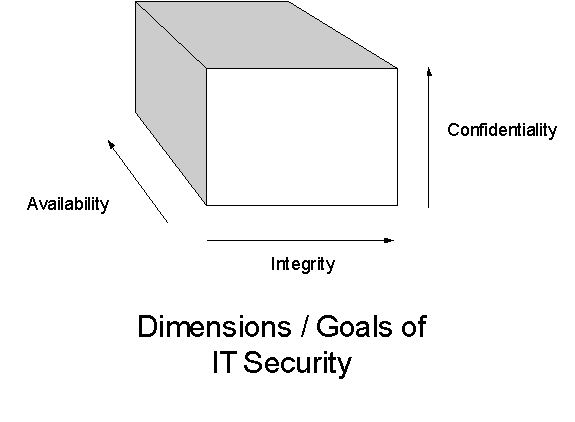
There is a fourth dimension that should also be considered, and that is time. The sad truth is that over time, due to the incessant nature of those who seek to undermine IT components and defenses, any IT system will become inherently more unstable and unable to provide the security that it was designed to provide. Thus, every level of IT security must be regularly reviewed for its ability to reliably provide these goals of IT security.
World’s Most Secure Computer
See Figure 1 below for a picture of the world’s most secure computer. It is in fact a database server with a database and SQL Server 2000 on it. It sits in a locked room in a secure area of our building. It is not powered up, or even plugged into an electrical outlet. And it is not connected to any network. Only two other people know it is there. It is totally secure from all forms of the typical threats that face most operational computers. It is also not very useful, or usable in its present state, but it is very, very secure.

Figure 1 – The World’s Most Secure Computer – Compaq Proliant 6000
Threats to Data Security
Unfortunately, many people take a very simplistic view of data security, thinking that if the database resides on a server that is inside the walls of a company, it will be safe and sound. However, that is quite simply not the case. See Figure 2 below.
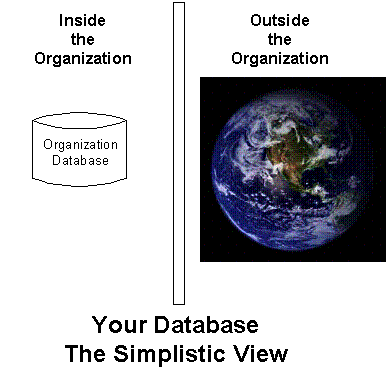
Figure 2 -- Your database – The Simplistic View
The reality is that there are many threats that can undermine your database. A representative list is shown in Figure 3 below. Notice the resemblance of the appearance of the black dots to bullet holes. This is intentional, to graphically illustrate that these threats will shoot holes in your database security.
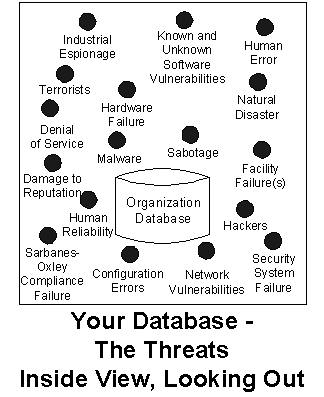
Figure 3 -- Your Database, Inside View, Looking Out
Common Database Server Threats
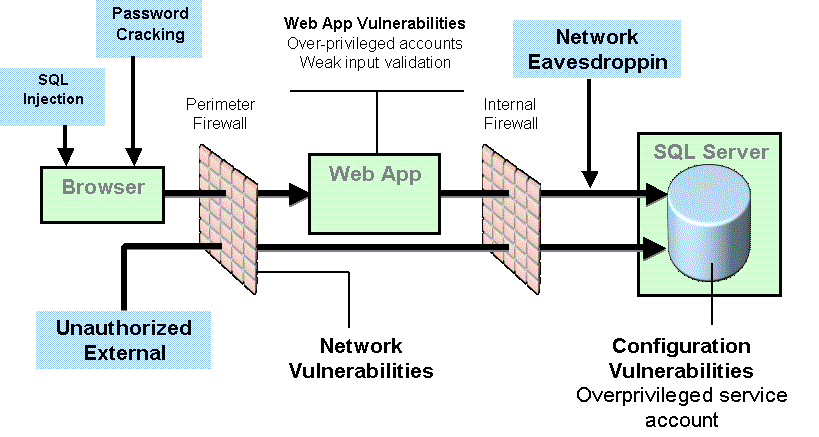
Figure 4 below illustrates real-world threats that individually and/or simultaneously threaten your production database server that is exposed to the Internet via a network connection (Microsoft 2004).
Figure
4 -- Common Database Server Threats
What Is the Weakest Link?
Studies show that the majority of problems in IT security come from within a company. These breeches in security come from employees, as a result of one of three things:
1) Being careless and not following good security practices as defined in the company security policies and procedures
2) Becoming a victim of a social engineering attack.
3) Acts of theft or sabotage, perpetrated by a disgruntled employee.
Therefore, a key component to any security plan, as well as IT security policies and procedures MUST be a human reliability program, where employees are educated about the risks, and monitored, surreptitiously and overtly, to ensure that if and when risks become elevated, they are dealt with in a measured response.
What Are the
Requirements for Data Security?
The table below succinctly shows the requirements of data security.
|
Requirement |
Description |
|
Physical Database Integrity |
The
data of a database are immune to physical problems, such as power failures,
and someone can reconstruct the database if it is destroyed through a
catastrophe. |
|
Logical
Database Integrity |
The structure of the database is preserved. With logical integrity of a database, a
modification to the value of one field does not affect other fields, for
example. |
|
Element
Integrity |
The
data contained in each element are accurate. |
|
Auditability |
It
is possible to track who and what has accessed (or modified) the elements of
the database. |
|
Access
control |
A
user is allowed access to only authorized data, and different users can be
restricted to different modes of access (such as read or write). |
|
User
authentication |
Every
user is positively identified, both for the audit trail and for permission to
access certain data. |
|
Availability |
Users
can access the database in general and all the data they are authorized. |
(Pfleeger and Pfleeger, 2003)
What Are the
Steps Toward Data Security?
The table below shows the basic steps toward data security.
|
Step |
Description |
|
Physical Security Control |
Allow
physical access to areas by authorized personnel only. |
|
Password
Security |
Allows the assignment of access rights to specific
authorized users. Password security
is usually enforced at logon time at the operating system level, but can also
usually me implemented and managed at the RDBMS level. |
|
Access
Rights |
These
can be established there the use of RDBMS software. The assignment of
specific access rights will restrict operations (CREATE, UPDATE,
DELETE, etc.) on predetermined database objects such as database files,
tables, views, queries, and reports. |
|
Audit
logs |
These
are normally provided by the RDBMS to check for access violation and to see
patterns in dates times that people are accessing the database. Although an audit log is an after-the fact
device, its mere existence can discourage unauthorized use. |
|
Data
encryption |
This
can be used to render data useless to unauthorized users who might have
violated some of the database security layers. |
|
Diskless
workstations |
These
allow end users to access the database without being able to download from
their workstations. On such devices,
the USB ports and access to the Internet should also be considered. |
(Rob and Coronel, 2001)
Check
List of Actions for IT Security and Database Security
The following checklist is from information gleaned from a presentation on Application Security given in April 2004 at the Microsoft Security Summit (Microsoft, 2004). Most of these are related directly to the database server and making your data more secure. These are not suggestions; they should each be taken very seriously.
|
Category |
Action |
|
Basic Security Configuration |
Test,
then Apply service packs and patches in a timely fashion. |
|
Disable
unused services and processes |
|
|
Network
Security |
Restrict
Database Server to utilizing only to
TCP/IP for communications |
|
Harden
the TCP/IP stack |
|
|
Restrict
ports; block all unnecessary ports |
|
|
Operating
System Security |
Configure
the SQL Server service account with the lowest possible permissions |
|
Delete
or disable unused accounts |
|
|
Secure
authentication traffic |
|
|
Database
Server Logons and Roles |
Use
a strong system administrator (sa) password |
|
Remove
the SQL guest user account |
|
|
Remove
the BUILTIN\Administrators server login |
|
|
Do
not grant permissions for the public role |
|
|
Category |
Action |
|
Files,
Directories, and Shares |
Verify
permissions on SQL Server installation directories |
|
Verify
that Everyone group does not have permissions to SQL Server files |
|
|
Secure
setup log files |
|
|
Secure
or remove tools, utilities, and SDKs |
|
|
Remove
unnecessary shares |
|
|
Restrict
access to required shares |
|
|
Secure
registry keys with ACLs |
|
|
Database
Server Security |
Set
authentication to OS only |
|
If
you must use RDBMS authentication, ensure that authentication traffic is
encrypted |
|
|
Database
Server Auditing |
Log
all failed OS login attempts |
|
Log
successful and failed actions across the file system |
|
|
Enable
RDBMS login auditing |
|
|
Enable
RDBMS general auditing |
|
|
Category |
Action |
|
Securing
Database Objects |
Remove
the sample databases |
|
Secure
stored procedures |
|
|
Secure
extended stored procedures |
|
|
Restrict
access to powerful stored procedures, like those that execute external
commands to the sysadmin role |
|
|
Using
Views and Stored Procedures |
SQL
queries may contain confidential information
|
|
Implement
security best practices for Web-based applications |
|
|
Securing
Web Applications |
Validate
all data input |
|
Secure
authentication and authorization |
|
|
Secure
sensitive data |
|
|
Use
least-privileged process and service accounts |
|
|
Configure
auditing and logging |
|
|
Use
structured exception handling |
(Microsoft, 2004)
Backups
One of the most important considerations for the security of databases, as well as all other types of data stored on computer disks, is the issue of backups. In order to ensure maximum protection, backups must be taken regularly, including nightly backups, either differential or incremental. However, differential backups are preferred over incremental because the restore process is simpler. Full backups need to be taken weekly, and of course there should be a last full backup of the month, which is the monthly backup. Weekly backups should be sent offsite for a period of three weeks and then rotated back on site and retained for a total of 12 weeks. The same is true for monthly backups, except they should be retained for 13 months. The yearly backup, which are full backups that will be taken at the end of each year, should be retained for six years or longer if deemed necessary. Remember to ensure that all media that is sent to offsite storage must be sent with a report of which servers and tapes go together, as well as complete restore instructions just in case the site should have to be reconstituted elsewhere.
It is also essential that backup media is regularly and carefully monitored to ensure that the quality of the backups is sufficient to conduct a restore, if it is necessary.
Finally, backups must be tested by doing periodic restores, to ensure clarity of the restore instructions, and the integrity of the media.
Hardware Reliability
Unlike software, which becomes more mature and stable over time, as the UNIX operating system has, hardware reliability becomes more uncertain as a component approaches the end of its useful life. This is why components are rated with estimated numbers such as Mean Time Between Failure (MTBF). The MTBF is the average expected life of a hardware component, expressed in hours. The MTBF of each disk component in a server, as well the power supplies, cooling fans, etc. must be documented with the IT asset inventory, so these can be carefully monitored and planned for replacement as they each near the end of their useful life.
High Availability
Though Digital Equipment Corporation perfected clustering technology in the 1980s with VAX/VMS clusters, companies like Microsoft, HP and others have taken the state of the art in clustering to provide high availability to new levels of excellence. And whereas a clustering solution used to costs in the hundreds of thousands of dollars, now it is possible to provide one for a fraction of that cost. It therefore makes great sense to provide a cluster for the production database when the business case justifies it.
Defense in Depth
As the field of IT security has matured, the areas that require defending have been defined in a set of commonly grouped areas shown in Figure 5 below, along with some specific categories that fall within these areas. The term for this layered model is known as “Defense in Depth” and it can be used in developing the organization IT security plan, to ensure that every area that stands between the outside world and your database, has been considered and addressed with some kind of security solution (Microsoft, 2004).
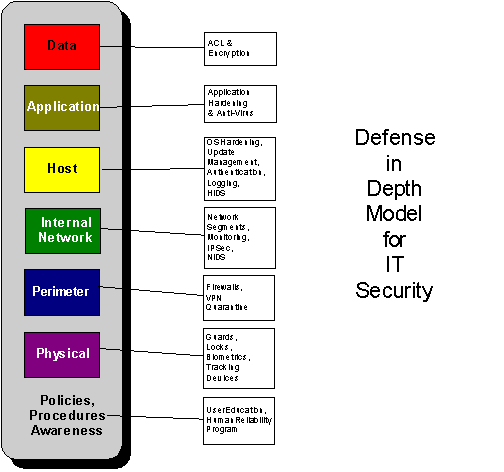
Figure 5 -- Defense In Depth – The Layered Approach to IT Security
Testing To Ensure Reliability
In order to assure that every area of your security plan and your Defense in Depth model of security is reliable and effective, tests and audit should be conducted on a regular basis. As deficiencies are noted, corrections and improvements should be made. There are two general types of audits, the Black Box Audit and the White Box Audit.
Black Box Audit
In a black-box audit a tests is only provided with a range of IP addresses to scan and probe for known vulnerabilities, much the same as a hacker would. Sometimes this is known as vulnerability scanning or penetration testing. Advantages of Black-Box audits include that fact that they are faster, cheaper and simpler than White-Box Audits. Disadvantages of Black-Box Audits include the fact that they will not uncover configuration errors, errors in policies and procedures, and errors in design (Norberg, 2001). See Figure 6 for a diagram of a Black-Box Audit.
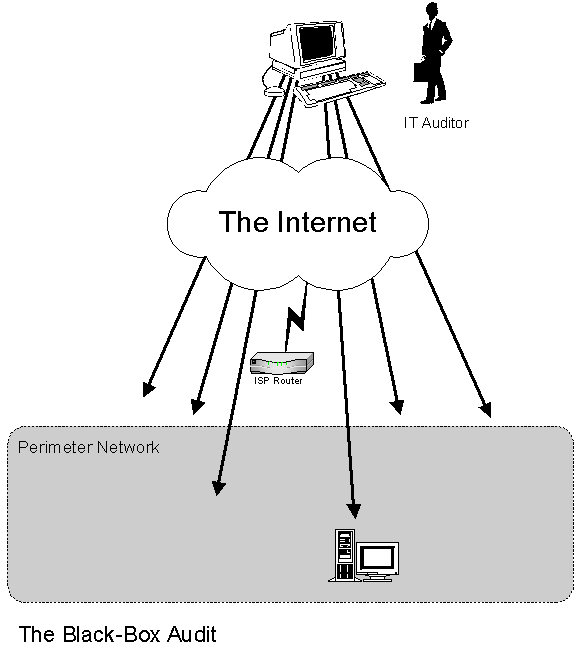
Figure 6 -- Black-Box Audit (Norberg, 2001)
White Box Audit
As shown in Figure 7 below, the White-Box Audit will involve auditors working inside your site. “They will require all possible information about your site, including network diagrams, configuration files, all available documentation of the systems. Using all this information, the auditors will be able to identify possible theoretical attacks against your environment. The auditors should also review and comment on your policy documents, for example your backup policy (Norberg, 2001).” Norberg recommends the White-Box approach over the Black-Box approach, despite its additional consumption of resources and additional length of time, because it will pay off in terms of finding more problem areas and vulnerabilities. The end result, if you follow through on their recommendations will be a more secure facility and IT resources.
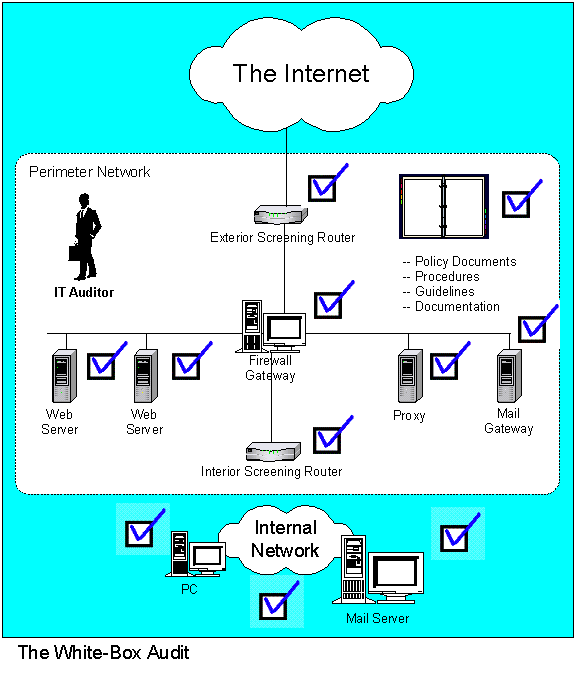
Figure 7 -- White-Box Audit (Norberg, 2001)
Design of a Security Plan
In order to design an effective Security Plan, all IT assets must be inventoried and all systems and networks must be defined and documented. Then, each threat must be recognized and met with some kind of relevant security solution. Following the Defense in Depth model shown above, each component of the IT infrastructure must be considered and assigned some kind of security solution, in order for the database to be as secure as possible. And the security plan must allow for regular review and testing, to ensure the necessary levels of IT security are maintained throughout the organization.
Security Plan -- The Payback
According to Aber, a well-planned,
well-executed and comprehensive security plan will help mitigate:
·
Theft of
proprietary information.
·
Financial
fraud.
·
Insider network
abuse.
·
Virus and worm
attacks.
·
Denial-of-service
incidents.
·
System
penetration by outsiders.
·
Legal
liabilities resulting from a breach.
(Aber, 2003)
Business Continuity and Disaster Recovery Planning
The Disaster Recovery Plan (DRP), and the Business Continuity Plan (BCP) are the tools that every business must develop, but they hope that they never have to use. We are all aware that the world is a much more different and uncertain place. Having a well-written and strenuously tested DRP, is the best way to ensure that the organization will have data it needs and the access to it, in order to continue operations should a worst case scenario occur. And a key component to having a viable DRP is having tape backups that we are certain will be reliable. It also includes having documentation with those tapes, in the form of tape / data / server association lists, as well as clearly written restore instructions. The DRP also specifies how, where, when, and on what equipment the data will be restored. This DRP is a key part of the BCP. The BCP specifies how the organization will reconstitute and continue its operations after it has been subjected to a catastrophe. The process of creating and maintaining DRPs and BCPs, is so complex, time consuming, and especially political in nature, that some larger organizations have actually created VP level or director level positions with titles such as VP of Business Continuity. In any case, both DRP and BCP should always be taken very seriously, and each are always carefully reviewed during an in-depth IT Security audit.
Policies, Procedures, and Training
Note that in the Defense in Depth diagram shown above as Figure 5, all areas are surrounded by a shape that specifies policies and procedures. Nothing in an organization ever gets accomplished without a plan, as well as policies and procedures that are implement to describe how the work will get done and how the on going IT Security Program will be administered. The policies and the program must be clear, and they must spell out responsibilities and consequences, if they are to be taken seriously. After they are created, they should be posted in on the organization Intranet, in a format that is easy to read and to print. In addition, these policies and procedures should be part of the employee training program, to ensure that each and every person knows their roles and responsibilities with regards to every facet of IT security. Remember, as these policies and procedures are created that they are helping product one of the organization’s most critical and valuable assets: our data.
IT Security Specialists
It is also recommended that you hire one or more security specialists to help create your Security Plan, and to help get your Security Program kicked off.. These would be IT professionals who have both extensive security-related experience, as well as security-related, professional credentials such as CompTIA’s Security+, the Microsoft Certified System Engineer: Security (either Windows 2000 or Windows 2003), the SSCP by (ISC)2, and/or the CISSP by (ISC)2. Of course the ideal candidate will also have an extensive background in being a database administrator in the same type of database environment that you need to secure. Such professionals devote themselves and their careers to solving IT security problems, and they will be able to address your security needs with the highest quality solutions in the shortest period of time.
Sarbanes-Oxley
The Sarbanes-Oxley Act, which was passed into law during Summer of 2002, will in June 2004 start to become the law of the land in terms of forcing corporate executives to accept full responsibilities for the veracity of their data and the reports that they file. Along with these requirements, come new regulations that deal with strict accountability in terms of management of IT assets. Having the solid plans in place which cover all aspects of IT security, as well as business continuity and disaster recovery, will help ensure that the leadership of an organization is not help criminally liable for failing to comply with the provisions spelled out in the Sarbanes-Oxley Act of 2002.
It Pays To Be Paranoid.
As trite as this expression sounds, there is actually some truth in it. Every good security person I have ever known, and I have known many, was rather paranoid, because each one knew the entire range of threats that could compromise various areas of the organization. Being paranoid was even popularized in Andy Grove’s popular book of the late 1990s, Only the Paranoid Survive. It was his premise that being paranoid was as an actual survival skill, because without this sense of paranoia, you would not be alert to dangers, real or imagined, that can threaten your existence. So while this should not be carried to the extreme, or be allowed to be a debilitating situation, I believe that being aware of the nature threats and new threats, as well as the ever increasing rate at which these threats occur, is probably a good thing.
Recommendation
A project needs to begin to create an organizational security plan. Out of this plan should come the policies, procedures, and processes that will improve the data security and the overall state of IT security in this organization. Also out of this plan should come the creation of as IT Security Program, led of a Security Director that reports to the CIO, who will administer the program. And due to the dangers that exist from both external and internal threats, I strongly suggest that this project commence sooner than later.
Conclusion
The issues surrounding the review and improvements in data security as IT security overall are indeed complex and continually evolving, because the challenges and the various technologies are continually evolving. It is nevertheless useful to take the areas of IT security and define them, as in the Defense in Depth model, assigning security solutions at each level to help ensure that what needs to be secure, will be. So it is imperative that we quickly implement a security plan and a security program, following principles and ideas in this document. Our new IT Security program should help us adequately secure our IT resources and at the same time help us be constantly vigilant against continuously emerging threats, as well as the never ending exposures that arise from software and hardware that were developed with security as an afterthought. On the bright side, if the right people are chosen to lead and implement this, and if they are found to be a good fit, we should have then around for years if we treat them right. Because the complexity of IT security, both in its breadth and depth, mandate that you have good security people on site to help implement and lead your IT Security Program. This is not a job that should be for the faint of heart, or even for offshore outsourcing.
References:
Aber, R. (2003). A Comprehensive Approach To Security. [Electronic
version]. Retrieved from the web on May 1, 2004 at http://www.bcr.com/bcrmag/2003/05/p17.asp.
Escamilla,
T. (1998). Intrusion Detection: Network
Security Beyond the Firewall. New York:
John Wiley.
Galik, D.
(1998). Defense in Depth: Security for Network-Centric Warfare. [Electronic
version] Retrieved from the web on May 11, 2004 from http://www.chips.navy.mil/archives/98_apr/Galik.htm.
Microsoft. (2004). “Implementing Application Security.” A presentation
delivered at the Microsoft Security Summit in April 2004. [Electronic version]. Retrieved from the web on April 21, 2004
at http://www.connect-ms.com/technet
.
Norberg,
S. (2001). Securing Windows 2000 Servers for the Internet. Beijing, China:
O’Reilly & Associates.
Pfleeger, C. P. and Pfleeger, S. L.
(2003). Security in Computing, Third Edition.
Upper Saddle River, NJ: Prentice Hall.
Rob, P. and Coronel, C. (2001). Database Systems: Design, Implementation, and Management, Fifth Edition. Boston: Course Technology.