Cyberwar Writings, Presentations, Resources, and References
William F. Slater, III, M.S. in Cybersecurity
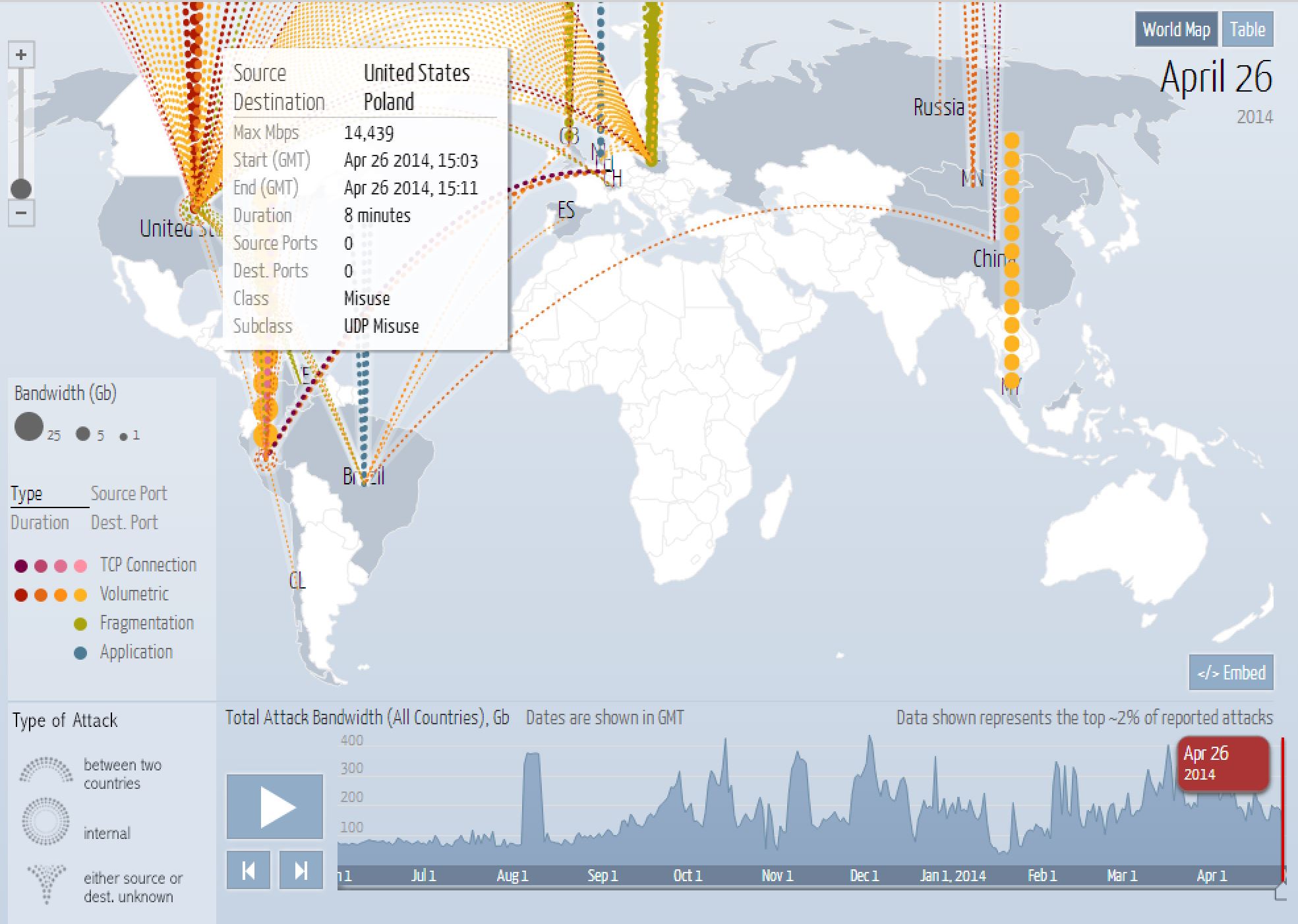
(click map or scroll down)
A 2002 article I wrote on the October 2002 Internet_Outage_and DDoS_on the 13 DNS Root Servers
Presentations
Suppose They Gave a Cyberwar and Everybody Came?
- Presentation for Northshore ASIS - August 8, 2013 (PDF version)
Suppose They Gave a Cyberwar and Everybody Came? (on YouTube.com)
Suppose They Gave a Cyberwar and Everybody Came? (PDF version)
What's in Presidential Policy Directive 20 (PPD 20)? How It Will Affect America and Americans and Why You Should Care (on YouTube.com)
What's in Presidential Policy Directive 20 (PPD 20)? How It Will Affect America and Americans and Why You Should Care (PDF version)
Real-Time Resources
Kaspersky Real-Time Cyber Threat Map
References
Beidleman,
S. W. (2009). Defining and Deterring Cyber War - Homeland Security Digital
Library. Retrieved from
https://www.hsdl.org/?view&did=28659 on March 18, 2013.
Bousquet, A. (2009). The Scientific Way of Warfare: Order and Chaos on the
Battlefields of Modernity. New York, NY: Columbia University Press.
Carr, J. (2012). Inside Cyber Warfare, second edition. Sebastopol, CA: O’Reilly.
Crosston, M. (2011). World Gone Cyber MAD: How “Mutually Assured Debilitation”
Is the Best Hope for Cyber Deterrence. An article published in the Strategic
Studies Quarterly, Spring 2011. Retrieved from
http://www.au.af.mil/au/ssq/2011/spring/crosston.pdf on October 10,
2012.
Fayutkin, D. (2012). The American and Russian Approaches to Cyber Challenges.
Defence Force Officer, Israel. Retrieved from
http://omicsgroup.org/journals/2167-0374/2167-0374-2-110.pdf on
September 30, 2012.
Gray, C.S.
(2013). Making Strategic Sense of Cyber Power: Why the Sky Is Not Falling.
Retrieved from
http://www.strategicstudiesinstitute.army.mil/pubs/display.cfm?pubID=1147
on May 26, 2013.
Hyacinthe, B. P. (2009). Cyber Warriors at War: U.S. National Security Secrets &
Fears Revealed. Bloomington, IN: Xlibris Corporation.
Kramer, F. D. (ed.), et al. (2009). Cyberpower and National Security.
Washington, DC: National Defense University.
Libicki, M.C. (2014). Why Cyberwar Will Not and Should Not Have Its Grand Strategist. Retrieved from http://www.au.af.mil/au/ssq/digital/pdf/spring_2014/libicki.pdf .
Libicki, M.C. (2012). Cyberspace Is Not a Warfighting Domain. Retrieved from http://moritzlaw.osu.edu/students/groups/is/files/2012/02/4.Libicki.pdf.
Libicki, M.C. (2009). Cyberdeterrence and Cyberwar. Santa Monica, CA: Rand
Corporation.
Markoff, J. and Kramer, A. E. (2009). U.S. and Russia Differ on a Treaty for
Cyberspace. An article published in the New York Times on June 28, 2009.
Retrieved from
http://www.nytimes.com/2009/06/28/world/28cyber.html?pagewanted=all on
June 28, 2009.
Obama, B. H. (2012). Defense Strategic Guidance 2012 - Sustaining Global
Leadership: Priorities for 21st Century Defense. Published January 3, 2012.
Retrieved from
http://www.defense.gov/news/Defense_Strategic_Guidance.pdf on January
5, 2012.
Saadawi, T. N. [Editor], and Jordan, L. H. Jr. (2011) [Editor] . Cyber Infrastructure Protection. Strategic Studies Institute. Retrieved from http://www.strategicstudiesinstitute.army.mil/pubs/display.cfm?pubID=1067 on May 26, 2013.
Saadawi,
T. N. [Editor], et al. (2013). Cyber Infrastructure Protection: Vol. II.
Strategic Studies Institute. Retrieved from
http://www.strategicstudiesinstitute.army.mil/pubs/display.cfm?pubID=1145
on May 26, 2013.
Technolytics. (2012). Cyber Commander's eHandbook: The Weaponry and Strategies
of Digital Conflict, third edition. Purchased and downloaded on September 26,
2012.
Turzanski, E. and Husick, L. (2012). “Why Cyber Pearl Harbor Won't Be Like Pearl
Harbor At All...” A webinar presentation held by the Foreign Policy Research
Institute (FPRI) on October 24, 2012. Retrieved from
http://www.fpri.org/multimedia/2012/20121024.webinar.cyberwar.html on
October 25, 2012.
U.S. Army. (1997). Toward Deterrence in the Cyber Dimension: A Report to the
President's Commission on Critical Infrastructure Protection. Retrieved from
http://www.carlisle.army.mil/DIME/documents/173_PCCIPDeterrenceCyberDimension_97.pdf
on November 3, 2012.
U.S. Department of Defense. (2013). Department of Defense - Defense Science
Board – Task Force Report: Resilient Military Systems and the Advanced Cyber
Threat, published January 2013. Retrieved from
http://www.acq.osd.mil/dsb/reports/ResilientMilitarySystems.CyberThreat.pdf
on March 16, 2013.
U.S.
Strategic Command information (2013).
https://www.facebook.com/billslater/posts/10152788814120456
Wagner, K. (2013). The NSA Is Training 13 Teams of Covert Hackers to Attack
Other Countries. And article published on March 13, 2013. Retrieved from
http://gizmodo.com/5990346/the-nsa-is-training-13-teams-of-covert-hackers-to-attack-other-countries
on March 19, 2013.
Articles at http://www.cyberwarzone.com
Papers at http://billslater.com/writing
Papers at
http://billslater.com/cyberwar
More References
Rand Beers is the current Under Secretary of Homeland Security for National
Protection and Programs. Beers was appointed as Under Secretary by President
Barack Obama on June 19, 2009.
March 20, 2013, he delivered this 12-page report, a Statement for the Record
Before the United States House of Representatives Appropriations Committee
Subcommittee on Homeland Security. It gives unusually detailed review of how the
Executive Branch, particularly the Department of Homeland Security sees its role
in defining and protecting Critical Infrastructure, both physical and virtual
from cyber threats related to cyberattacks. It also discusses the contents the
contents and intent of PPD 21, EO 13636, both of which are related specifically
to cybersecurity and protection of critical infrastructure.
For your edification:
http://appropriations.house.gov/uploadedfiles/hhrg-113-ap15-wstate-beersr-20130320.pdf
More information:
EO 13636
http://blog.zwillgen.com/wp-content/uploads/2013/02/CybersecurityEO-201302122.pdf
PPD 21
http://blog.zwillgen.com/wp-content/uploads/2013/02/PPD21-201302124.pdf
Update Presentation on the OBAMA Administration Priorities on DHS Highlights
Efforts to Strengthen Cybersecurity for the Nations Critical Infrastructure
http://www.dhs.gov/news/2013/02/13/dhs-highlights-efforts-strengthen-cybersecurity-nations-critical-infrastructure
Commentary:
http://blog.zwillgen.com/2013/02/13/for-obama-a-cybersecurity-triple-play /
= = = = = = = = = = = = = = = = = = = = =
= = = =
Quotes in News
Articles
= = = = = = = = = = = = = = = = = = = = = = = =
=
This is
the link is James Temple’s article in the San Francisco Chronicle regarding
recent computer security threats and issues.
Internet is still vulnerable to cyber-criminals
--James Temple, Chronicle Columnist, Saturday, January 21, 2012
I was one of his subject matter experts that he interviewed for the article. He
found me because of a 2002 article I wrote for the
Internet Society about DDoS attacks on the 13 DNS Root Servers in October 2002.
Other Cybersecurity-Related Writing
M.S. in Cybersecurity at Bellevue University
Visitor Count
Copyright 1996 - 2013 by William F. Slater, III,
Chicago, IL, USA
All
Rights Reserved, Nationally and Internationally.
|